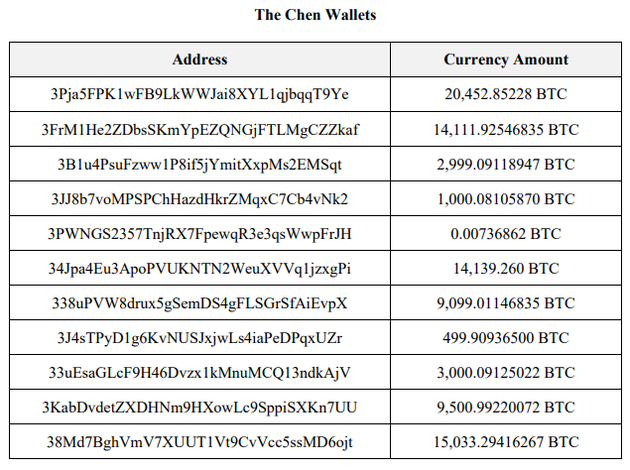
The U.S. Department of Justice (DOJ) has announced a major financial enforcement action, filing criminal charges and a civil forfeiture complaint against Chen Zhi, the founder and chairman of Cambodia's Prince Holding Group. The DOJ is seeking to permanently seize approximately 127,271 Bitcoin (BTC), valued at over $15 billion, linked to the group.
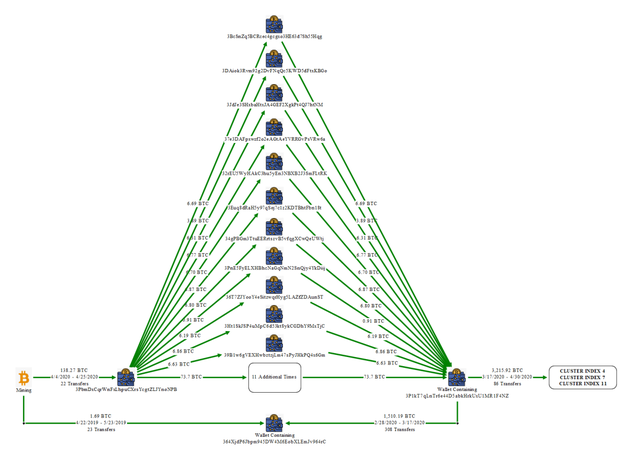
The case has drawn global attention because this massive hoard of cryptocurrency was not held in regulated, centralized exchanges. Instead, the BTC was scattered across 25 non-custodial wallets where Chen Zhi allegedly held the private keys. The U.S. government not only successfully traced the on-chain assets but also achieved the unprecedented feat of effectively seizing the private keys and transferring the assets.
The theoretical bedrock of cryptocurrency security has long been "Not your keys, not your coins," implying that without the private key, no one—including governments—can move the funds. This successful seizure has led many to question how U.S. law enforcement bypassed what was widely considered the "security fortress" of non-custodial wallets.

Photo/Court file
The Mystery of the Private Keys: Insider Leak or Technological Breakthrough?
Experts interviewed by National Business Daily (NBD) offered several hypotheses:
Cooperation of a Witness: Yan Lixin, Executive Director of the China Centre for Anti-Money Laundering, Fudan University, suggested that an insider, such as a technical lead within the group, provided the wallet seed phrases or private keys under judicial pressure.
"Weak Randomness" Exploit: Max He, Chief Scientist at Singaporean digital asset service provider Safeheron, pointed to the technical possibility of "brute-forcing" private keys from wallets generated with weak random number generators (PRNGs). He referenced the "MilkSad" White Hack Project, which demonstrated that wallets using seeds set to a small 32-bit integer have a vastly reduced key space (only $2^{32}$) and can be recovered through extensive searching.
"Inside Man" or Physical Seizure: Xiao Sa, a legal scholar and Senior Partner at Beijing Dacheng Law Offices, proposed the possibility of an "inside informant" within the criminal organization or a coordinated international law enforcement effort with countries like the UK and Cambodia to seize hardware devices containing private key backups during raids.
The Criminal Enterprise: Forced Labor and Sophisticated Money Laundering
Photo/FBI
Court documents reveal that since 2015, Chen Zhi allegedly used the Prince Holding Group's extensive business network across over 30 countries to secretly operate at least ten forced labor fraud compounds in Cambodia. Workers were allegedly lured, imprisoned, tortured, and forced to run massive crypto investment scams (known as "pig butchering" scams), defrauding victims of billions of dollars. To maximize efficiency, the complexes housed professional "mobile phone farms," with two facilities alone controlling approximately 76,000 social media accounts. The U.S. Treasury estimates that U.S. losses from Southeast Asian scams alone could reach $10 billion in 2024.
To clean the illicit proceeds, the group established an intricate money laundering system:
1. "Money Laundering Houses" (Water Houses): These specialized houses employed "spraying" (splitting large sums into countless small transactions and distributing them to hundreds of new addresses) and "funneling" (re-aggregating the dispersed funds back into a few core addresses) to sever the on-chain link to the source of the funds.
2. Cryptocurrency Mining: Chen Zhi allegedly used the ill-gotten gains to purchase mining equipment and pay electricity costs, boasting of "considerable profit, no cost." This mining operation provided a "legitimate income" façade, replacing "dirty" crypto with newly minted, "clean" Bitcoin to circumvent regulatory scrutiny. The system was characterized by Yan Lixin as a "dual-track cooperative" laundering architecture.
The Secret to Precision Targeting
The key to identifying the assets was the FBI's "intelligent upgrade of on-chain analysis," according to Yan Lixin, involving:
Graph Neural Networks (GNNs): Building transaction graphs to automatically identify abnormal patterns like "multi-address clustering and high-frequency small transfers," boosting identification efficiency by 300%.
Reverse Exploitation of Mixers: Analyzing the UTXO (Unspent Transaction Output) associations of mixers like Tornado Cash to trace funds back to their original injection points.
Cross-Data Source Correlation: Fusing blockchain data with dark web chat records and exchange IP logs to pinpoint the physical location of wallet users.
Yan Lixin highlighted three specific techniques: Chainalysis Reactor for linking multiple addresses to a single "funds cluster" by identifying common transaction signatures; Mixer Tracing, which successfully recovered over 7,000 BTC from the Sinbad mixer; and Multimodal Data Fusion for creating a complete evidence chain from victims to the criminal group by integrating KYC data and intelligence.
Non-Custodial is Not a Free Pass

Photo/VCG
The successful seizure of the Bitcoin has fundamentally challenged the notion that non-custodial wallets are beyond the reach of law enforcement.
Yan Lixin stressed that this case proves that even with decentralized storage, a combination of "on-chain tracing + off-chain evidence collection" can achieve effective recovery, debunking the misconception that "non-custodial wallets equal a legal sanctuary."
Max He added that true security hinges on the rigor of the entire cryptographic implementation chain. "If a single link is weak—such as insufficient randomness, flawed key storage, or unaudited code—attackers can find a breakthrough."
Building a Comprehensive Anti-Money Laundering Framework

Photo/VCG
Experts agree that the Chen Zhi case marks the entry into a "technology-driven anti-money laundering" era. Yan Lixin proposed a "tripartite regulatory system" covering legislation, technology, and international cooperation:
Regulatory Framework: Extending Anti-Money Laundering (AML) laws to include new sectors like NFT and DeFi, and strengthening Know Your Customer (KYC) obligations for Virtual Asset Service Providers (VASPs).
Technological Empowerment: Developing independent on-chain analysis tools utilizing AI to identify risks such as "high-frequency transfers and cross-chain money laundering," shifting from reactive to proactive intervention.
International Collaboration: Deepening joint enforcement actions, actively aligning with FATF standards, and facilitating cross-border intelligence sharing through bodies like the Egmont Group.
Industry Self-Discipline: Encouraging VASPs to establish "risk-based" internal controls and creating "black-list sharing platforms" to quickly block at-risk funds across institutions, echoing agreements like Tether's real-time freeze protocols.


 川公网安备 51019002001991号
川公网安备 51019002001991号





